I don't want public ISPs to know that I am selfhosting my services at XYZ IP.
I have experimented with various solutions. Tor hidden services, double hop VPNs, mTLS exposed websites, Mesh networks like Tailscale, Headscale or Netbird, Cloudflare tunnels or Pangolin tunnels, etc..
None of them provide me with the solution I am looking for, so I set out with a few goals:
- I wanted to be able to access my homelab services.
- I wanted that access to be behind a commercial VPN (namely Mullvad, as they are the only public VPN i currently trust).
- I want to route all other traffic through Mullvad.
- I wanted to be able to access my homelab services on Android and Linux, without requiring a rooted android device.
- I do not want to rely on a third party service to provide security (E.G Cloudflare, Tailscale, etc...)
- I want to have my data be key protected. It should not just be exposed publicly for anyone to locate.
Attempted Solutions
Mesh Networks
- Android does not allow for two active VPN connections at a time without rooting or having one run in userspace mode.
- Currently no mesh networks (Tailscale / Netbird / etc...) support running in userspace mode. Someone has created a userspace Tailscale proxy, however I have not had success in allowing it to work with a separate VPN provider at the same time.
- If you are stuck behind CGNAT with no way out, this or tunnels may be your only options.
Tor Hidden Services
- Tor Hidden Services do work. You can use this on Android and Linux; its annoying to setup and has the standard performance issues with Tor.
- Apps do not natively support Tor hidden services. That means you need to create a local reverse proxy that will proxy your domains / IPs to Tor.
How to:
- Expose your selfhosted services as Tor Hidden Services via Onionpipe or other Tor service.
- Set up LocalRelay on your client device
- Use your LocaRelay address as the address you are trying to connect to for your various services
Double Hop VPNs
- There is a way. Using an external router allows you to tether your device with a split tunnel VPN to route your homelab services to your homelab VPN, and then a commercial VPN on said router.
- If you are following our phone guide, this is the option we would recommend. For those who don't want to, there are easier options below.
- As far as I am aware, since I cannot control the config for Mullvad's servers, I am not able to set up a standard double hop / chained VPN. If it possible, let me know how.

Tunnels
- Pangolin / Cloudflare require you to trust a third party server. Whether that server is Cloudflare's or a VPS you rent, you are still necessitating a server that you trust.
- This poses additional risk via a public server acting as a MITM proxy that is out of your control.
- This adds an additional hop to your routing (Mullvad -> Pangolin/Cloudflare -> homelab). Additional hops will degrade speed and increase latency.
- If you are stuck behind CGNAT with no way out, this or mesh networks may be your only options.
mTLS
- Apps do not support mTLS out of the box. That means you need to create a reverse proxy that contains a mTLS certificate in it, and proxy your data to your various apps.
- Drawbridge / Emissary is an app combo that is supposed to do that, however, I have yet to get it to work effectively. It also does not support domains, and so you will need to use localhost and memorize ports. This can be annoying if you have many services.
Port Forwarding
- Some VPN providers support port forwarding for easier access. However, I do not trust any of them personally, and would rather just roll with Mullvad. If you do, you can set up port forwarding via that VPN provider and access your homelab that way.
Actual Solution
Proxy Chains
Proxy chains are how I have managed to find a working version that only requires your server with Wireguard and a commercial VPN provider.
To do this, I am using Nekobox(ray) to connect to both my commercial VPN (Mullvad) and my homelab's VPN.
- Nekobox runs a single VPN service in Android kernel mode. It then selectively proxies the connection based on the routing rules.
- While there are other apps that also do this, Sagernet, Sing-Box, etc... Performance on them was degraded. I am getting 50ms latency and 150 Mbps throughput on 5g with Nekobox, in comparison to the dropped connections -> 5 Mbps on other apps.
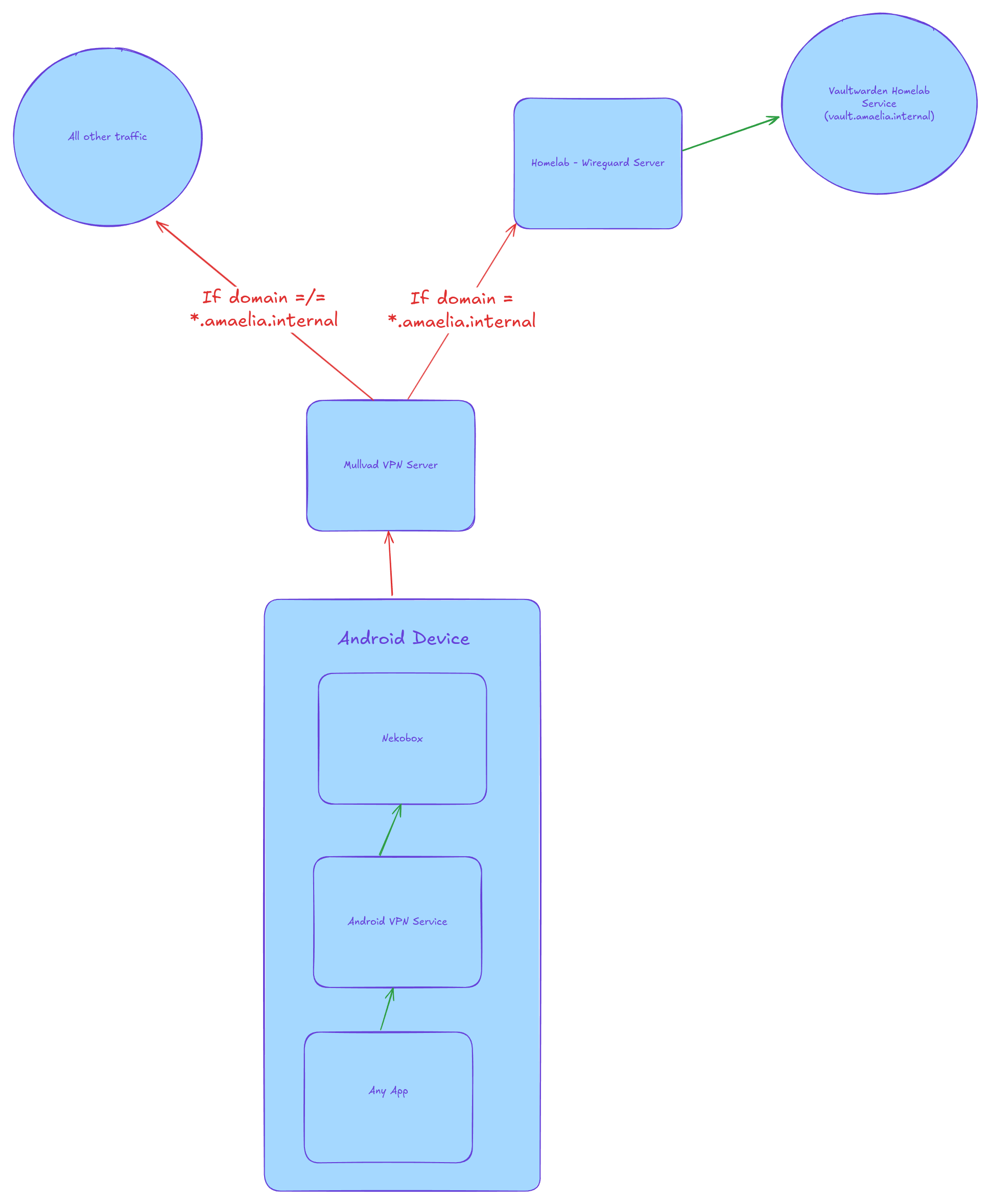
How to:
- Set up a Wireguard VPN using WG-Easy, WG-Dashboard, or your other favorite VPN or Proxy service.
- Nekobox accepts quite a few proxy frameworks, but I just stick with Wireguard
- Nekobox requires a
mtuin your config file to auto import - addMTU = 1420to your .conf file.
- Import a Wireguard config for Mullvad into Nekobox with a mtu. Name it
Mullvad - Import your homelab's Wireguard config into Nekobox. Name it
Homelab - Create a proxy chain with
Mullvadfirst, followed byHomeLabcalledChain - Go to Nekobox route and add the following two rules.
- Rule 1
- under
Domainput your homelab's internal domain. For me, that isamaelia.internal - under
OutboundselectSelect Profileand then putChain
- under
- Rule 2
- under
Domainputregexp:.*- This matches every domain in regex
- under
OutboundselectSelect ProfilethenMullvad
- under
- Since your internal domain rule is triggered first, it will match that domain and send all relevant data through your proxy chain. For all other data, it will go through just Mullvad.
- Rule 1
- Turn on
Chainin Nekobox
And now, all traffic should go through Mullvad, with only your homelab traffic going through your proxy chain through Mullvad, to your homelab! Success. You can repeat this configuration with Nekobox for Linux to get your laptop setup as well!